
Tell me, did you have a tamagotchi in the 90s?
Unlike the silly toys from the 90s, pwnagotchi is a working hacker tool for hacking wireless networks. It is fed by network packets sent by wireless clients during the handshake or handshake stage.
To brighten up your drab routine and introduce a game element into the network hacking, pwnagotchi has a mood-change algorithm, similar to the original Tamagotchi. And the main thing is to feed him more often, so he does not get bored. However, you can keep him company. Pwnagotchi is capable of finding their own companions and joining together for joint attacks.

It is possible to customize pwnagotchi by giving it a unique appearance:
https://github.com/evilsocket/pwnagotchi/blob/master/pwnagotchi/ui/faces.py
The pwnagotchi system is based on a neural network, and therefore has the ability to learn. Besides, its functionality can be extended with plugins, which implement such functions as: automatic software update system, backup creation, linking captured handshakes to GPS coordinates, publishing data about hacked networks to onlinehashcrack.com, wpa-sec.stanev.org, wigle.net and PwnGRID, additional indicators (memory consumption, temperature, etc.) and performing dictionary matching of passwords for hijacked handshakes.
According to the authors of pwnagotchi, they wanted to create something new, but from available components that would not need to be designed from scratch. As a result, the hacker “Tamagotchi” was based on the Raspberry Pi Zero W single-board computer.
The creators of pwnagotchi noted that the choice of the basis for the toy is not limited to a single computer model. In fact, any single-board PC manufactured by Raspberry will do, including the earliest models.
Installing
To build a pwnagotchi you need: a Raspberry Pi 0 WH (or Raspberry Pi 0 W, but you need to buy additional GPIOs), a Waveshare 2.13″ (preferably the second revision), a micro-sd card from 8 gigabytes and a battery/overbank to power the device.
When everything is assembled you can install the firmware, for this you need to download Win32 Disk Imager utility and the firmware itself:
https://sourceforge.net/projects/win32diskimager/
https://github.com/evilsocket/pwnagotchi/releases/
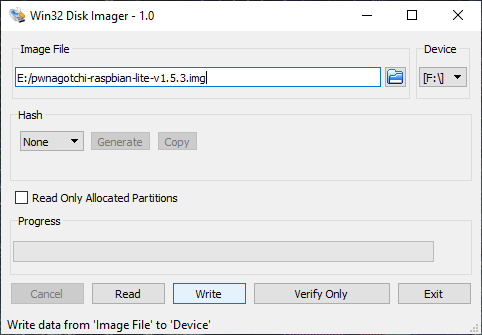
After the recording is done, before powering on you can specify a name for pwnagotchi and an access point that you do NOT want to hack (your home network, for example) by creating a config.yml file in the boot section, where you should put the following:
main:
name: 'pwnagotchi'
plugins:
grid:
enabled: true
exclude:
- 'YourHomeNetworkMaybe'
report: true
whitelist:
- 'YourHomeNetworkMaybe'
ui:
color: 'black'
display: ~
enabled: true
type: 'inky'
After the system boots (the first startup may take ~ 2 minutes) pwnagotchi will start scanning access points and collecting handshakes.
Connecting to a computer
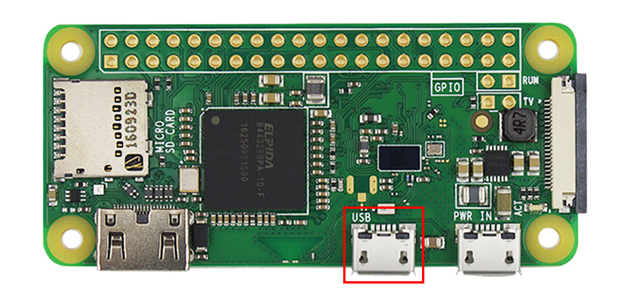
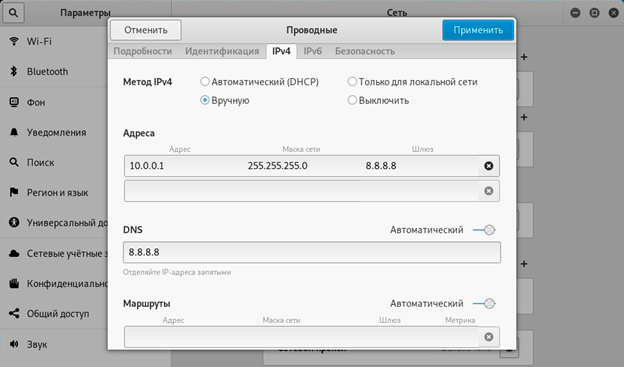
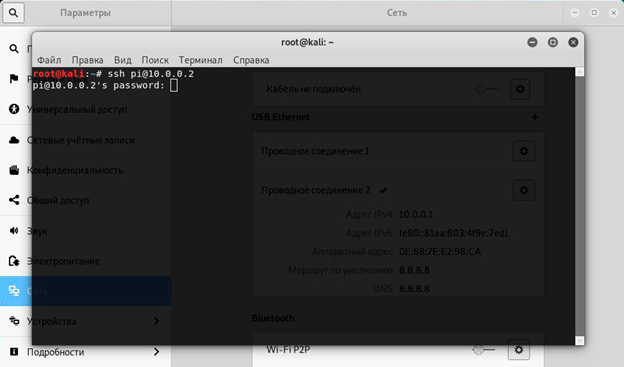
Connect via the second (data) slot, then a new device should appear in the adapters section (Ethernet 2 in my case), he needs to prescribe ipv4 and the netmask manually as in the screenshots below, then we can connect via ssh, command ssh pi@10.0.0.2 (user pi, password raspberry).
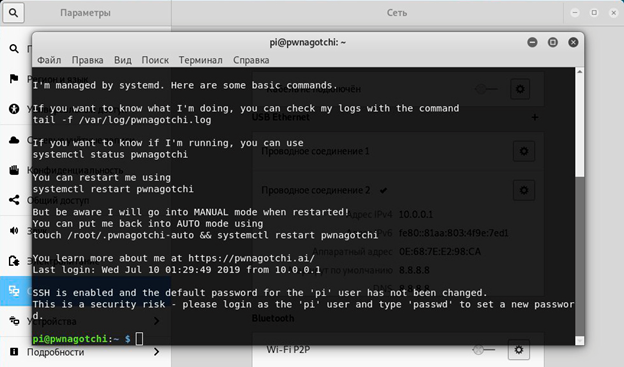
How do I get handshakes collected by pwnagotchi?
After at least one handshake is collected, you will see PWND at the bottom of the screen, and next to it the number of collected handshakes and the number of access points whose handshakes have already been collected.



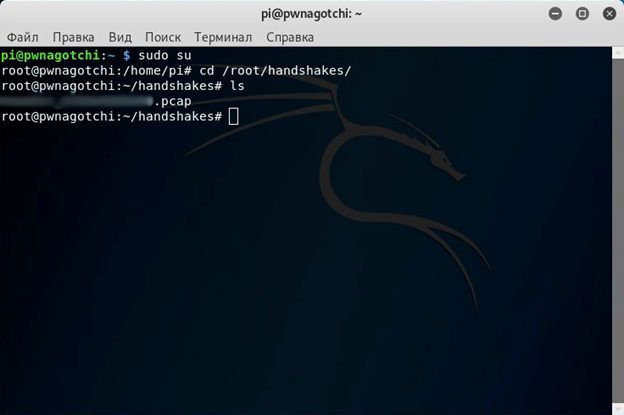
You can retrieve the handshakes (by default they are stored in /root/handshakes) via ssh, with the command
scp pi@10.0.0.2:/root/handshakes/name.pcap /home/username/Desktop/
Remember that using pwnagotchi without the permission of the owners of Wi-Fi networks is a criminal offence, as it can be classified as an attempt to gain unauthorized access. According to the law, you can be imprisoned for up to five years or pay a large fine for doing so.
Never use the methods described in the article. This article is written for informational purposes only. The author is not responsible for the application of the skills. Otherwise, you are breaking the law.