Does everyone know the word deanon? And it’s not at all about the fight against anonymity. With the help of cunning technology, everyone is identifying you – from advertising and media agencies, to big data collectors, to various government agencies. The problem is very serious, and in this article we’ll touch on just the tip of the iceberg and talk about how to at least somewhat secure your online experience.
The widespread use of digital fingerprinting technology makes it easy to collect personal information. In addition, users share personal information on their own on social networks, messengers, email and other online platforms, often without knowing that their data can fall into the wrong hands.
In the first part we figured out what fingerprinting is and made Firefox a little safer. In the second part we will talk about how to hide fingerprinting, setting up a virtual machine, anonymous and not quite browsers and of course about protecting your identity online.
VirtualBox setup.
It’s no secret that a virtual system has a very peculiar config and digital footprint. You don’t even need to use software like AIDA64 or EVEREST to make sure. Just open “Device Manager”. Your whole system just “screams” that it is a virtual machine.
Here I will describe some manipulations of the VM to make its fingerprint less recognizable and hide the very information that it is a virtual machine.
We will use VBoxHardenedLoader:
This is a great add-on for VirtualBox that allows you to change almost any parameters of your virtual machine.
Just downloading the file is not enough. You also need to make the necessary settings. To do this, follow the manual.
Download and install VirtualBox.
Open VirtualBox and create a virtual machine with the settings you want.
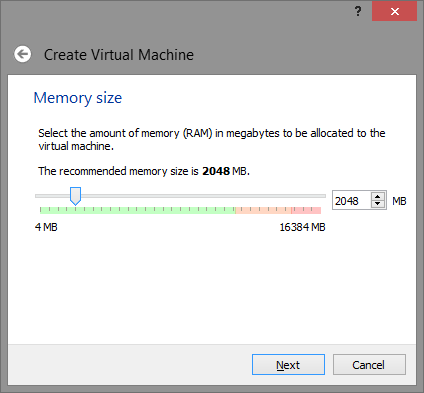
Note: 2048 MB is not mandatory, you can adjust or reduce this value at your discretion, but keep in mind – some detection systems try to identify the virtual machine by the available amount of physical memory and if it is too small – it is a red flag indicating that it is a virtual machine.
Create a virtual disk.
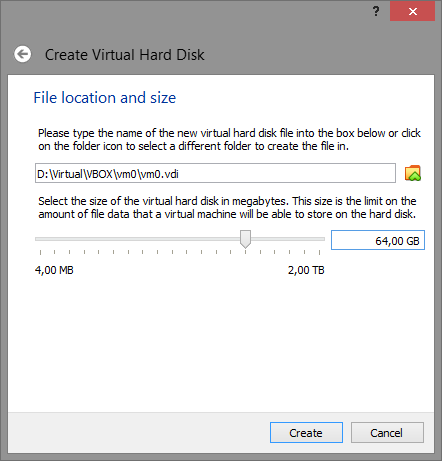
Remember that the recommended disk size should be 32 GB or better 64 GB. A smaller size will be an indication that it is a virtual machine.
Once the virtual machine is created, open its settings – you will need to make certain changes.
In the System menu, Motherboard tab, check the Enable I/O API checkbox.
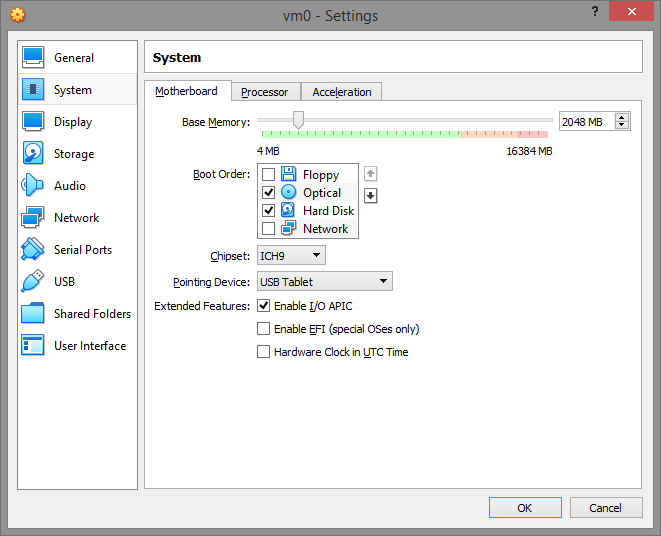
In the Processor tab, enable PAE/NX and set at least 2 processors. If only one processor is indicated, this is an indication that a virtual machine is being used.
In the Acceleration menu, set the Paravirtualization Interface to Legacy and turn on VT-x/Nested Paging. If you leave paravirtualization set to “Default” it gives the virtual machine the Virtual Box hypervisor and even the hypervisor name through the cpuid value. And that’s total crap!
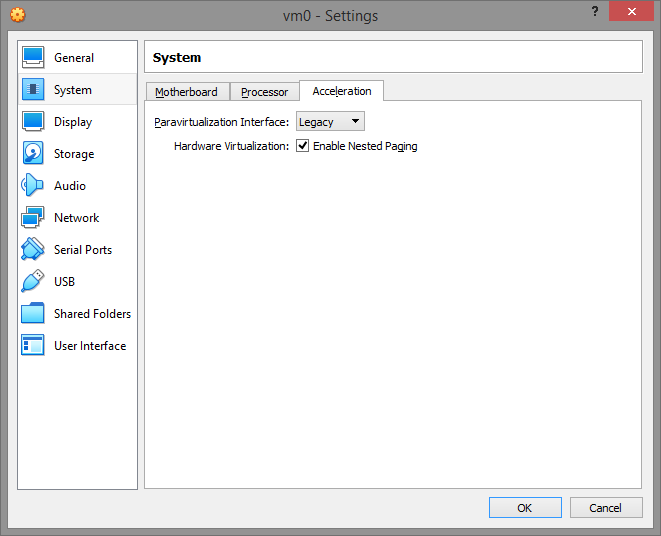
On the Display tab, turn off 2D/3D Acceleration.
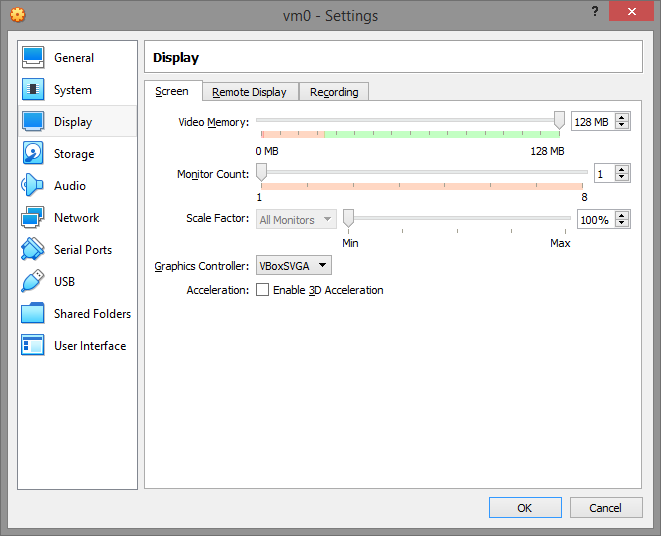
Storage.
It should look something like this.
Save all settings and close VirtualBox completely.
Download the software from here and save it wherever you like. For example c:\vboxldr.
Now the important part. Go to the data folder and choose the system startup script.
hidevm_ahci for VMs with SATA/AHCI controller and classic BIOS
hidevm_ide for VM with IDE controller and classic BIOS
hidevm_efiahci for a VM with a SATA/AHCI controller and EFI
hidevm_efiide for VM with an IDE controller and EFI
Edit the script according to your configuration to fit your needs:
set vboxman=”C:\Program Files\Oracle\VirtualBox\vboxmanage.exe”
set vmscfgdir=D:\Virtual\VBOX\Settings\
Change vmscfgdir to the settings folder of your machine.
Make the rest of the settings and run the script with the name of your virtual machine.
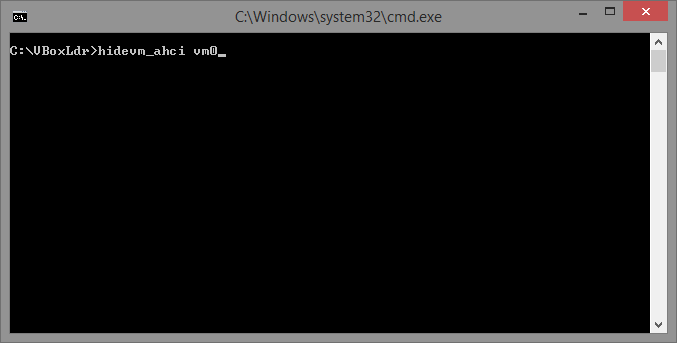
But don’t run VirtualBox – you’re not ready yet.
Run loader.exe with Administrator privileges.
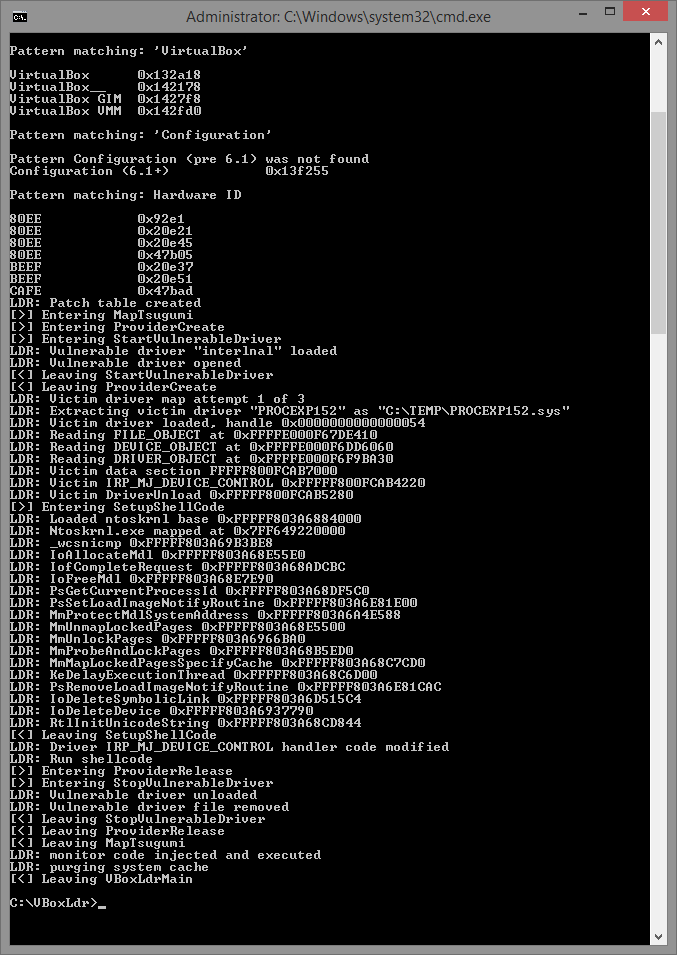
You will have to repeat this step every time you restart the OS.
Warning! Remember that you must not install Virtual Box Additions in any case – it will ruin everything.
As practice shows, each configuration needs its own approach to installation and its own writing of config file. Much depends on the operating system and its version, on which we are going to build a virtual machine.
In the flexibility and reliability of the system can not be doubted. Everything is set up individually to your taste.
Let’s replace all the hardware of our virtual machine:
- processor model
- motherboard manufacturer/brand
- BIOS ID, version/date
- CPU ID and HDD ID
- Windows Product ID
- video card swap (Important!)
- random Mac-Adress of the network device or install for each machine manually
- unlike a simple virtual machine, on ours we can control the parameters of the sound card (a hint of audio fingerprint swapping), but of course we still need to work manually on this and install the necessary software.
Through VboxHardenedLoader give our future virtual machine random properties and parameters, and then install itself there Windows. All the settings of our miracle machine must be made before the first start of the operating system. That is, your virtual machine is already running with these settings as a full PC and will be identified as someone’s PC, not a virtual machine with VVOH prints.
You can see how to set this up in this video:
How to work with the virtual machine?
When you create a machine, let’s call it the MAIN machine, you load all the necessary software into it, set up the anti-detect browser, etc.
The ready MAIN machine will be cloned, and in the future we will work only with its clones. After “working out” clones can be removed and, if necessary, make other clones. Don’t forget to make the clones different from the MAIN VM, remembering that this is a cloned machine and it is similar to the MAIN. We need it to be different. Run the written config file and everything happens automatically. VboxHardened does its job.
One click clone randomization works with all hardware except CPU and motherboard.
You don’t have to change CPU model that often, as long as it is different from the host CPU model. It is important that the CPUID itself has changed. The final choice is yours – when, how and how often to change the model.
For the paranoid, the tuned machine (and later clones) can be used in conjunction with Whonix. You can add to this the neighbor’s Wi-fi.
Configuring VMWare.
There is also a commercial virtual machine from the pioneers of the virtualization topic. Although in VMWare the hardware configuration is not as flexible as in VirtualBox with add-ons, it is possible to hide the fact that it is a virtual machine without any add-ons or plug-ins, by your own means.
I used VMWare Workstation for Win.
1) It requires a newly installed system, how to make changes to an existing system – have not found.
Prepare a virtual drive, specify the system, as you normally do, and in the settings for the machine to be installed, I have this item is called Isolation, turn off any exchange of data with the host OS.
2) Next, you need to find the VMX configuration file created at the stage of creating the machine in VMWare, and at the end add lines:
isolation.tools.getPtrLocation.disable = "TRUE"
isolation.tools.setPtrLocation.disable = "TRUE"
isolation.tools.setVersion.disable = "TRUE"
isolation.tools.getVersion.disable = "TRUE"
monitor_control.disable_directexec = "TRUE"
monitor_control.disable_chksimd = "TRUE"
monitor_control.disable_ntreloc = "TRUE"
monitor_control.disable_selfmod = "TRUE"
monitor_control.disable_reloc = "TRUE"
monitor_control.disable_btinout = "TRUE"
monitor_control.disable_btmemspace = "TRUE"
monitor_control.disable_btpriv = "TRUE"
monitor_control.disable_btseg = "TRUE"
These options prevent programs from detecting the virtual environment through complex checks such as memory address space, counters.
Important: If at the installation setup stage there are options like “Express install”, “Quick install” – turn them off. Also do not install VMWare Tools in installed system, as some software includes presence of this package in check.
3) Save the file, specify to download ISO with the system installer, install OS as usual.
4) Despite the fact that the vast majority of programs which don’t like virtualization don’t go further than the checks we’ve cut off at Step 2, some very stubborn ones go further and try to find, for example, everything that looks like the name of virtual disk controllers.
To defeat them in Windows as well, we go to the registry editor, to the HKLM\SYSTEM\CurrentControlSet\Services\Disk\Enum branch. As you can see, there is a very clear reference to the fact that the disk is virtual.

We need to change it by removing VMware, Virtual, Ven, etc, and keep it that way.
It also makes sense to replace in the registry search for VMware/Virtual on some Intel or IBM everything that changes, not just disk variables.
After that, try to run your stubborn object of experimentation – in 70% of cases, the described steps will help to pass virtual environment checks.
Important: The value in HKLM\SYSTEM\CurrentControlSet\Services\Disk\Enum is overwritten after every reboot, so it must be changed after every new system start.
And more about virtual machines
Structure your virtual machines
We strongly recommend dividing your Internet tasks into several categories, and using a separate virtual machine for each of them. For example, use one machine for accessing personal mail, banking, government services, and other very personal sites. For accessing social networks, use a different machine. Use a third for surfing the Internet. For work – a fourth. Believe me, it’s not that complicated. Don’t be lazy and set everything up once. After all, security is paramount.
Testing?
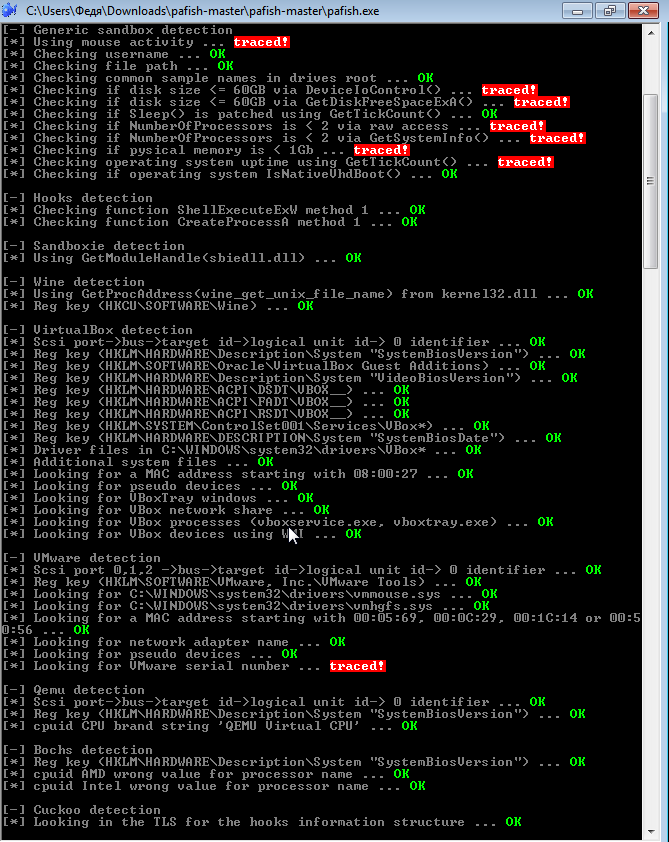
You can use Pafish to check whether you are safe from detection, as well as other sandbox and virtualization detection tools that are popular among developers.
Bypassing Fingerprints.
Let’s start with what methods of identification exist, and then move on to ways of bypassing/disabling them.
A common way websites get your data is by using cookies. Cookies are small packets of text files that are stored on your computer and contain certain data, which can provide websites with information to improve your user experience.
Each time you visit a website, your browser will download a cookie. When you visit the same website later, it will check the data packets and provide you with a customized user experience.
Think about the font size or screen resolution that you are viewing on the website. If the website knows that you always use an iPhone 8, it will give you the best settings for your iPhone. In addition, this way, the site knows whether you are a unique visitor or a returning visitor. Cookies also store data about your browsing habits, interests, and more.
In addition, websites use Javascript, which will interact with visitors to perform certain tasks, such as playing videos. These interactions also trigger a response, and so they get information about you.
To identify the user’s browser and without cookies, digital fingerprinting technologies have emerged. The most widely used are Canvas fingerprint and WebGL fingerprint. Perhaps the most popular library for digital fingerprinting is FingerprintJS2, written by our compatriot Valentin Vasiliev: https://github.com/Valve/fingerprintjs2. Updates were made a few months ago, so development is active.
One of the most effective methods to protect against browser fingerprinting is to disable JavaScript and Flash.
When JavaScript is disabled, websites cannot detect the list of active plugins and fonts you use, and they also cannot set certain cookies in your browser.
The disadvantage of disabling JavaScript is that websites don’t always work properly.
Flash, on the other hand, can be disabled without negatively affecting websites.
Font Fingerprint.
When exactly when the technology appeared is unknown, but the fact that the technology of font fingerprinting has found its application in almost all major antifraud companies is no longer a secret. This technology obtains a list of fonts installed on the user’s PC.
To protect the user needs to disable Adobe Flash and JavaScript in your browser.
Conclusion – it’s worth turning it off if you just surf the net and want to be anonymous, and you need a spoofing to work.
The easiest way to spoof fonts is to zoom the page. You can pick up an extension in Mozilla for this if you want.
There are tests of this fingerprint on the web, you can try it.
WebGl Fingerprint.
The technology is responsible for acceleration and graphics and is part of Canvas.
Microsoft at one time called for abandoning WebGL because of its vulnerability to external attacks.
Its essence is that 3D triangles are drawn, then effects, gradient, different anisotropic filtering, etc. are applied to it. It is then converted into a byte array, which is still attached various information about platform-dependent constants that are defined in WebGL. These constants are very much, their dozens – this, and the color depth, and the maximum size of textures, etc. etc.. As a result, all this information is added to our image of a 3D triangle.
The version of the drivers, the version of the video card, the OpenGL standard in the system, the version of the shader language, will all affect how this image will be drawn internally. And when it is converted to a byte array, it will be different on many computers.
Information about the user’s video card is communicated through the fingerprint.
What to do, you ask. You can disable it with plugins, but we’re interested in swapping.
Since WebGl is part of Canvasa, it can be partially spoofed by using one of the Canvas spoofing plugins.
Complete swapping is done by manipulating the video card.
On the virtual machine we configured through VirtualBoxHardened, with the commands and parameters specified, it had its own footprint, different from the main one.
In such a machine in the Device Manager instead of “Virtualbox Graphics Adapter” you can see “Standard VGA graphics adapter” with its preinstalled with Windows drivers and identifiers. As a result, there is a complete substitution of the video adapter device in the virtual machine. When we installed Windows in the virtual machine, it didn’t see the VBox video adapter device there, as usual, but a full-fledged PC with its own hardware, so the drivers were installed exactly as we needed. Hence the fingerprint swap.
The Savas fingerprint.
The method itself is quite clear: when you enter any site, with user tracking code installed, such a resource asks the user’s browser to render a hidden image, and the text is drawn, using the fonts and renderer available to the system. The font set and anti-aliasing methods vary slightly from machine to machine. The renderer depends on the browser version, OS and even the GPU. In the end, the rendered image is unique.
There are different browser plugins that disable Canvas, such as this one:
https://github.com/kkapsner/CanvasBlocker
Mouse Fingerprint.
Widely used in various spheres – from the simplest anti-fraud systems to government surveillance programs.
Like many other things it is implemented via JavaScript
To protect against Mouse Fingerprint technology, it is recommended to disable JavaScript in the user’s browser.
Ubercookie.
A new technology that was invented by José Carlos, a researcher from Barcelona, allows to identify the user even in the TOP network.
According to Jose Carlos, Ubercookie technology is one of the main methods to de-anonymize users of the TOP network and is actively developed in the field of antifraud due to its effectiveness.
Evercookie (persistent cookie).
A small file gets on your PC. It multiplies and proliferates furiously through your system, hiding from you in hidden folders/files.
Evercookie is a very clever plugin that can save your data almost anywhere. Evercookie uses all available browser storage – modern HTML 5 standard, Session Storage, Local Storage, Indexed DB and others.
For the average user who does not know all this, it is simply impossible to delete these cookies. You have to visit 6-8 places on your hard drive, do a number of manipulations just to clear them. So the average user, when visiting a site that uses evercookie, will probably not be anonymous.
Despite all this, evercookie does not work in incognito mode.
For everyone else, there is of course a solution.
The way is to keep the system safe from this infection – a properly configured anti-detect machine will accept Flash cookies, Local Shared Objects-LSO cookies gladly, but they will all be sent to our RAM. As a result, the system sees that we have accepted the cookies, but, in fact, they did not fall on our PC, so they did not get registered there and could not unload, causing us harm. When we have finished working with the site, we close the browser window the cookies will be removed from memory.
WebRTC Fingerprinting.
WebRTC is a peer-to-peer communication standard over audio streams, or it is the standard for audio communication in modern browsers. It allows you to make audio calls, etc.
So why is it so dangerous? Because P2P asks for the user’s IP address during the exchange of information, and WebRTC kindly provides this information to everyone.
Even if the user is working via VPN or TOR with WebRTC site can easily find out your real IP address.
You can check at whoer.net or ipleak.net.
You can disable it, but it is better to hide your local IP from the WebRTC service. This solution exists. Bottom line, you have WebRTC turned on, but no IP is transmitted. Only your VPN, for example, will be detected.
Fingerprintjs2.
It appeared in 2012, the author does not sleep and updates his brainchild to this day. We wrote about it a little bit above.
Its essence is that the code of this library interrogates the user’s browser for all the specific and unique settings and data for this browser and for this system, for the computer.
The entire list of what the code asks for is listed here.
FingerprintJS doesn’t use cookies at all. No information is stored on the hard disk of the computer where the browser is installed.
It even works in incognito mode because it doesn’t use hard disk storage at all. It has no dependencies and its size is 1.2 Kb gzipped.
Currently used by companies such as Baidu, is Google in China, MasterCard, the U.S. President’s website, AddThis is a widget hosting site, etc. This library has quickly become very popular. It’s used by about 6-7% of all the most visited sites on the Internet right now.
This shows how it works.
Question: how unique and accurate is the definition? The study that was taken as the basis for this was done by the Electronic Frontier Foundation, they had a project called Panopticlick. It says the uniqueness is about 94%, but according to the developer on the real data that he had, the uniqueness was about 90%-91%.
Audiofingerprint.
The so-called audio fingerprint finishes our hit list.
The method works as follows: using the AudioContext API, low-frequency audio signals are sent to the user’s computer, then the way it processes them is determined, and a unique “audio fingerprint” is created. Despite the complexity, this method is extremely effective
With its help, law enforcement agencies and advertising services can de-anonymize users via VPNs without having to decrypt the traffic.
A study was conducted and out of 1 million websites, more than 80% had audio fingerprinting technology.
There is an online database from May 2016, there is a list of sites that use this fingerprinting.
At the moment, audio fingerprint technology is actively used by the U.S. intelligence agencies – FBI and NSA, Europe – Interpol, as well as gradually takes a leading position in anti-fraud systems around the world. This form of user identification is so unexplored that even the creators of the Tor browser since May 2016 unsuccessfully try to bypass it.
To protect against audio fingerprinting, it is recommended to completely disable JavaScript in the browser, but such drastic measures will lead to a complete inability to work with most sites.
Substituted through manipulation of the audio device configured on the above mentioned virtual machine.
Anonymous and not-so-anonymous browsers.
1 – Tor Browser.
Available on Windows, Mac and Linux.
The TOR network is designed for one simple task – anonymous communication. This browser is the most secure.
TOR allows you to hide your location, browsing history, forwarded messages, and other sensitive data from people or traffic analysis software.
This browser forwards traffic through many individual relays and tunnels in such a way that header analysis becomes meaningless. Simply put, instead of direct forwarding from point A to point B, there is forwarding through a network of many nodes.
A sniffer listening to only one node in that route would never know the source or the receiver of the intercepted information.
However, the TOR browser also has disadvantages, the main one being speed. Because the traffic is routed through many nodes, the pages may not load as quickly as you would like them to. If you have a good channel, this will not be a problem, but if you have a slow Internet connection, TOR web browsing can be annoying.
It should be noted that TOR is the best solution in terms of anonymity, but complete privacy is not guaranteed. For example, downloading torrents or illegally watching TV leaves you vulnerable. However, compared to well-known browsers such as Chrome and Safari, the TOR browser is far ahead.
2 – Epic Browser.
Available for Windows and Mac.
Although Epic Browser does not use a special onion network, it disables many options that negatively affect your privacy while surfing.
For example, history is not saved, DNS pre-fetching (used to speed up page loading) and cookies are disabled. Also, DNS cache and autofill forms are disabled.
After closing the session, the browser automatically deletes all related databases, settings, the contents of the Pepper Data folder, and cookies used by the flash player and the Silverlight plugin.
3 – SRWare Iron.
SRWare Iron is a free secure browser based on Chromium, optimized for maximum speed. SRWare Iron was developed by the German company SRWare as a secure alternative to Google Chrome browser, which does not protect 100% from tracking users by web-sites. SRWare Iron uses the latest version of WebKit and V8, the browser does not track user actions, thus providing a high level of security and privacy.
The main difference between Chrome and SRWare Iron is improved anonymity tools. Experts criticize Chrome for its use of “Unique User ID”. Every time a new session starts, Google is alerted to the use of your data.
SRWare doesn’t use Unique User IDs and other features that affect security, such as search tooltips.
4 – Comodo Dragon Browser.
Available for Windows and Mac.
Comodo does not even closely resemble TOR, but has some built-in tools to improve security while surfing. For example, it automatically blocks tracking, cookies and web spies. In addition, this browser has a built-in validation feature that separates strong and weak SSL certificates. It also uses anti-virus to protect against Trojans, viruses, and other attacks.
As with the previous browser, Comodo Dragon is designed based on Chrome. Accordingly, many users can easily switch.
And now for the not at all anonymous Brave.
You’ve probably heard of the Brave browser, but the company’s website explicitly states that the app is “anonymous” and monitors user activity. In addition, the default search engine is Google, which itself does not carry any anonymity. The browser’s home page connects to the brave.com homepage and sends certain requests in its direction; by default it includes crash reports, which are sent along with the browser (and possibly PC) characteristics and settings, each time Brave is turned on it will address requests that are clearly related to their advertisers, to provide targeted advertising. The browser blocks ads partially, you could say selectively, even when the ad blocker is on.
You can turn it off. But what about the switch?
Here we will only touch Firefox, I will tell you about other methods and browsers in the next article.
Go to browserleaks.com and let’s go.
Go to the left menu on the site and select JavaScript:
IP, WebRTC.
I will not talk about IP and WebRTC here. About these parameters they talk too much, and moreover, I will talk about WebRTC in a future article, namely how to organize his substitution in a virtual machine with one of the most powerful antidetection solutions.
But the link to article for general development about WebRTC I will throw:
http://incashwetrust.biz/podmena-webrtc.html
Flash.
IP merging over Flash – can not be skipped. Now, of course, many people do not have Flash installed on your desktop solution, but if you have it and you do not want to get rid of it – then you have to do the following manipulations:
You need to change the file mms.cfg (if Flash is installed on your computer).
If the file does not exist, then create a path:Windows (32Bit): C:\Windows\System32\Macromed\Flash\
Windows (64Bit): C:\Windows\SysWOW64\Macromed\Flash\
And put at the end of the file: DisableSockets=1
But it’s better to take it down after all, it’s almost useless nowhere. Because through it goes drain the same plugins.
Time.

We look at the system time. You’d think you’d set the time as the proxy/ip location and that’s it? No, that’s not enough. Some of the technical things that will leak you out:
- Appropriately the time itself and the match to the IP time zone.
- The system time has text in brackets (Moscow, standard time). Sometimes it happens so that it says, for instance, Saudi Arabia (I had such a problem on one of my computers), although the time settings in Windows are correct. As far as I think it is connected with the wind system itself and you can only change this by demolishing and reinstalling with a different image. All the virtual machines hosted on it had the same problem as Zennoposter.
- The deviation is in seconds. As you can see the difference between local and system here is 21 seconds. How many machines can there be with the same time deviation logging into Facebook accounts in a row? And even more so in the same IP subnet?
Language.
The language, namely the proportion from one (q=0.9 or 90%) of the user is determined by its history and cookies. The higher the value, the higher the probability that the user uses that language as his native language.
The value after the straight line in Header and JavaScript is determined by the settings in the browser. (In Chrome: Settings → Advanced → Languages → Language).


The value in brackets will be 100% different for different virtualizations with different history in the browser.
TCP/IP stack fingerprinting (Passive OS fingerprinting).

About the operating system, I will not discuss anything, virtualization closes this case for sure. The interesting thing here is the last parameter, TCP/IP.
What to read about it:
https://www.netresec.com/index.ashx?page=Blog&month=2011-11&post=Passive-OS-Fingerprinting
Briefly – MTU value for wired Internet and some Wi-Fi modems should be 1500 (maximum value).
For mobile operators 1400 or 1500 (sometimes less than 1400, usually a multiple of 10, such as 1380). Some usb modems have 1340-1380, the same usb modems have 1340.
Also text value (Windows NT kernel) gives out in you user not mobile operator, but desktop internet. For the same Android user there will be at least the text about Linux 2.2.x-3.x, etc. Sometimes for some (Megafon modem) there is a text about VPN.
What am I all about? If you emulate a mobile user, but sit from a modem – this point will turn you in the guts. Bad VPN/Proxy rental service providers, who don’t bother with similar security settings, will also “turn you in” with this item. And they may be able to solve the problem with the numeric MTU value, but there are few solutions with the text value on the market at the moment.
One solution: emulation of a mobile device happens – use the mobile device to distribute the Internet. From the desktop – of course desktop, modem, cable.
DNS.
I don’t see anything wrong with Google’s DNS (8.8.8.8 and 8.8.4.4), but at a distance using only it on one subnet is already a suspicious thing for the AI. Better, in my opinion, to use the default DNS of your subnet:
- Gives away the less experienced computer user in you;
- The distance to the DNS servers is closer (Google’s closest are in Finland);
- Different subnets – different DNS.
Navigator.
The data we need:
hardwareConcurrency – number of cores.
deviceMemory – number of GB of RAM.
In my opinion it is not necessary to swap them if they are more or less standard (for example 4 and 4). But if you have a machine with 32 GB of RAM – at a distance it will be a bad sign.
Here in terms of swapping I can not tell you anything (at least in this article at the moment, because I use my own templates for that). But in a future article I think I will.
The remaining data in the Navigator submenu is irrelevant, the virtualization closes the problem with it.
Plugins.
If chrome – you will be shown more or less the standard set of three plugins. Naturally, the site sees more of them. For this you should have a set of links to the most popular 25-30 plugins and install 2-3 plugins every time you configure your own anti-detect browser.
Location.
I see no point in discussing location, because if you set up your IP location properly, it will be tied to it.
Screen resolution and bit rate.
There’s no reason to get all weird and outdated with your computer’s resolutions. You can use the standard and most popular 1366×768 and do not care. Of course at a distance of 50-100 already need to change something, but I do not think that on this parameter will go negative from the simulation. Statistics of the most popular resolutions:
https://www.w3counter.com/globalstats.php
http://gs.statcounter.com/screen-resolution-stats
The bit rate of 24 is standard. And there is no point in changing it.
HTTP headers.
The virtualization also closes the problem with them.
JavaScript.
What do you things to pay attention to?
The screen resolution parameter has also such a parameter as viewport (the workspace in the browser). That is, because of the address bar and tabs in the browser, the task bar at the bottom with the start button and scrolling in the browser on the right – the resolution of viewport will differ in a smaller side from the screen resolution. This is worth considering if you emulate, for example, a resolution larger than the monitor screen size (let it be 1920×1080), but leave the viewport the same as it is at a lower resolution (for example the viewport 1349×657, which belongs to the resolution 1366×768). This will be very scary for detection systems, especially if it is repeated.
Parameter doNotTrack I do not touch, especially do not affect anything when working with the same virtual, rather forced change it already allows to think of you, as a more sophisticated user.
Battery Status API.
Specially checked if the latest version of Chrome has a drain on this parameter by unplugging my laptop. It does:

Consequently, when working from a laptop, you need to have a 100% charge and a constant connection to the network (when logging out and logging into different accounts, especially in the same subnet IP).
Web Audio API.
I will touch on AudioContext Fingerprint (below).
Installed Plug-Ins.
Covered in the last article. Keep a list of links to the 30 most popular plug-ins and randomly install 3-5 each time.
Silverlight.
Next, in the left menu, skip Flash (as discussed in the last article) and choose Silverlight.

If you see this inscription – then everything is fine and you have one of the latest versions of your browser (checked on the latest Chrome and Firefox), which does not support this outdated and insecure plugin.
In the same case, if it is present and you do not want to get rid of it, it is worth every time to clear all the data on your virtual (host) machine along the path:
C:\Users\%Username%AppData\LocalLow\Microsoft\Silverlight\is\
Java Applet.
Next item in the menu on the left side of the Java Applet.

As you can see, this is the same situation as with Silverlight. An outdated and insecure plugin that has been removed from support in new versions of browsers. So outdated that I can’t even tell you how to enable it. Do you need it?
WebGL.
I’ll give you a hint only with changing values: Unmasked Vendor, Unmasked Renderer and WebGL Report Hash (which changes after changing the first two). And only for Mozilla. The last one I’ll explain later in a future article.
To do that, just type in about:config, then search for Vendor and change it to whatever you want. For example, just Mozilla.

Next, enter Renderer and select webgl.renderer-string-override:
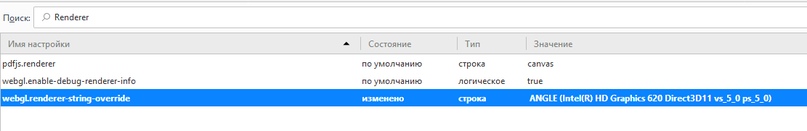
I entered for example ANGLE (Intel(R) HD Graphics 620 Direct3D11 vs_5_0 ps_5_0).
WebGL Report Hash should change too. But with Image Hash we will have to sweat. I’ll leave this point, maybe I’ll add it, but so far I don’t have a home-made solution to this point, I can only say that it’s different in different browsers. I do not need it, because I have my own self-written browser, where there is an automatic substitution of this point.
You can, of course, also block access to WebGL – but it is a powerful call to Zucker and quick subsequent ban.
WebRTC Leak Test.
With WebRTC I can single out one thing here – the so-called Media Devices. Again, this point is switched in my browser, but here I can suggest that you can add some devices to this list with the program Virtual Audio Cable (find it on torrents). Play with this program, it does not matter what parameters you change. The main thing is to change the final value of the audio print.
About the presence / absence of video camera and microphone – the request is provided by the site and the user confirms whether or not he wants to provide the site access to them. So there can’t be any leak here.
Canvas Fingerprint.
For Canvas fingerprint swapping, you can use the Canvas Defender extension. It’s available for both Mozilla and Chrome. Yes, it’s a palaver to some extent, for sure sites can pull up that you’re using this extension at the moment. But if there’s no other way out, you can do it that way.
As an alternative, in Mozilla you can go to Settings and find this section in the Basic menu:

Select Advanced and uncheck the box next to Allow websites to use their own fonts instead of the ones installed above. Let’s save the changes. And now choose the default font (supporting Cyrillic) with some size (preferably standard).
This will change our Canvas (like Font Fingerprint by the way).
Font Fingerprint.
As I said in the last article, you should have a set of fonts and randomly install some of them before you start a new virtual machine for example. I would add some thoughts of my own – it is necessary to install the most popular fonts (and to have a set of the most popular fonts). As at pulling by means of JS the site pulls installed fonts on its internal list (i.e. it can not expose your outlandish ones and will be similar to previous fillerprint). It can pull the entire list only with Flash, which has long been turned off for everyone.
Content Filtering.
That’s what I’m talking about. Canvas Protection gets dirty and the alternative solution is better in this regard.

Adblock stinks, it’s natural, but especially non-standard and repetitive set of blocklists will stink. The solution – do not use Adblock, or do not touch it in any way, not to be different from a group of people.
Features Detection.
Huge set to detect any working/non-functioning features on a machine. What can I say? When your account is banned on the virtual machine and you haven’t uninstalled Windows or cleaned everything thoroughly, it’s possible that this set is left and will give you away with its fingerprint on the next account. That is, do not install unnecessary drivers like KLite Media Codec Pack. Of course, you don’t need to look closely at every stage, but compare, for interest, what values you have on the host and virtual machine for Modernizr.video.h264 and for example Modernizr.jpeg2000 and Modernizr.jpegxr. On the host machine the h264 is probably true, but on the virtual machines it’s not. And the values with jpeg are both false. This is quite normal, but if there is something unusual and for a long time – it will again make an unfavorable imprint on you in the eyes of antifraud systems. You should not cling to this as one of the moments of the ban, but with a chain of values, where there will be a flush – it will play more negatively than the other way around.
More Tools.
Select More Tools next and I will explain some of the options:
Firefox Resources Reader – inactive because the leak was happening on older versions of Firefox. The leak was that Firefox would pretend that it was Firefox and leak some hashes of data that were stored in its JS files.
ClientRects Fingerprinting – the method of fighting is exactly the same as with Canvas. That is, changing the default font in Mozilla.
CSS Media Queries – should be different on different virtual machines.
Social Media Login Detection – one of the most interesting things in this article, since I haven’t seen any thoughts about it anywhere. As you will notice, the site will detect on your machine which of the social networks you are logged into. And Facebook will probably do the same before you check in. How uncomfortable it will be for it to be your very first social network to sign up for, don’t you agree? Keep this list to yourself and randomly sign up for some of them each time before you sign up.
audiofingerprint.openwpm.com
For the audio fingerprint, I use a separate site audiofingerprint.openwpm.com. As I said above, you have to play around with Virtual Audio Cable installed to change it. To check your fingerprint, click Fingerprint me!
How do you check your security?
There are several resources that use the same data collection methods but show you the weaknesses in your settings. By visiting these sites you can see how likely you are to be identified online:
Here you can check for data disclosure by your browser: https://browserleaks.com/.
And this site from American human rights activists will allow you to analyze your anonymity online: https://panopticlick.eff.org/
Another good resource showing exactly what flaws can compromise your anonymity online and how anti-fraud systems respond to these anomalies: https://www.whoer.net/
Are you still reading and not freaking out about all these methods of collecting your personal information? So you’re on your way with us and you care about yourself and your safety. And that means we’ll be sure to tell you how to keep yourself safe.
Take care of yourself and remember: safety is paramount. Don’t be lazy and set things up competently.
Never use the methods described in the article. This article is written for informational purposes only. The author is not responsible for the application of the skills. Otherwise, you are breaking the law.